MyITRisk Survival Guide

We are seeing an increasing number of security threats which our clients, and the world in general are facing. We are attending conferences and researching what is needed to keep you and your business safe even though we are not a cybersecurity company. Please understand there are no absolute guarantees with IT security. There are companies that do specialize in cybersecurity which detect breaches, mitigate attacks and do penetration testing.
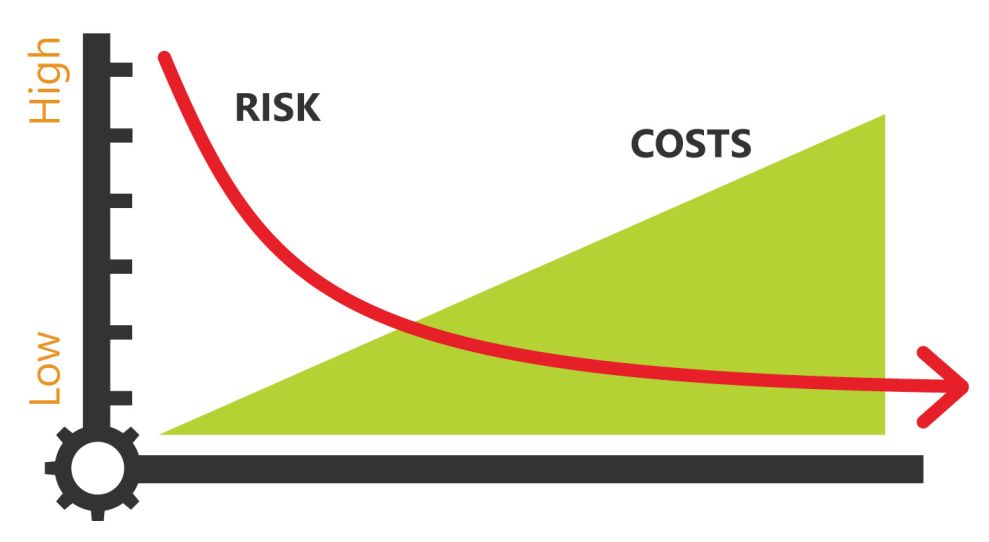
MyITRisk can guide you through cost effective improvements to lower your IT security risk, without having to engage a full cybersecurity company.
MyITRisk works with you to do the following:
-
Develop a company IT security plan and policies
-
Conduct user training and risk assessment
-
Create a financial plan covering: insurance, upgrades, budget, vendor negotiation
-
Identify, recommend and implement risk protections

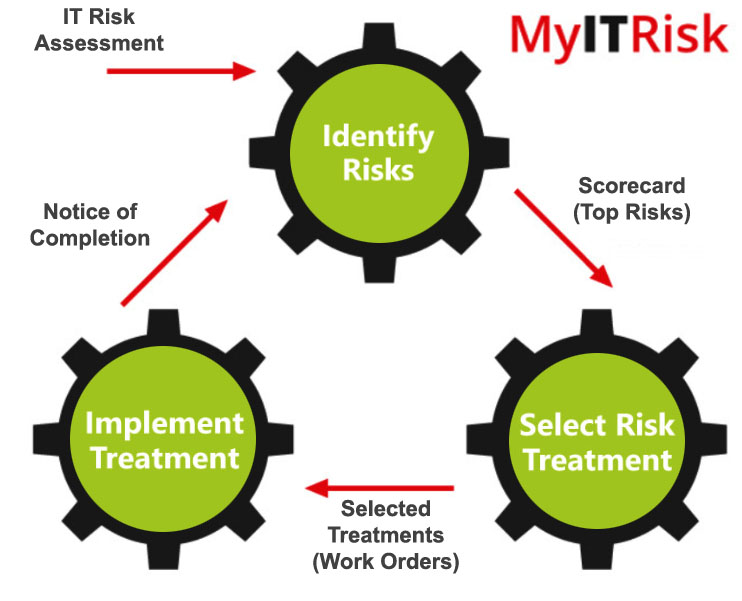
MyITRisk Process to reduce your IT security risk
Continuous cycle to implement needed improvements.
Your primary risk protections should include the following:
Multi-factor Authentication
- This works by text message, phone call to a mobile device, or an app to generate a code that your programs require to gain access
- Provides an additional layer of security to protect you from hackers
Benefits: This can prevent access to your accounts even if the password is compromised.
Email Safety and Protection
- Artificial Intelligence for spear email phishing detection
- Connects with office 365 and both blocks phishing attempts and reports to a dashboard that MyITRisk monitors on your behalf
Benefits: This reduces the risk of breach via email, which is still the most
often used method to breach your systems.
Endpoint Management Software
- Antivirus that reports problems to central dashboard viewable by IT
- Patch Management – keeps software up to date on security patches
- Asset Tracking – hardware and software management
- Secure IT access
Benefits: Plugs known vulnerability holes and protects from known threats
Data protection
- All user files stored in cloud (i.e. Dropbox, G-suite or Office 365)
- Server disk level backup off site, point in time recovery, ransomware protection
- Regular password changes, strong passwords, secure password management
Benefits: Recover from device failure, disaster and data breaches.
Web Filtering
- Firewall Content Blocking
- Server disk level backup off site, point in time recovery, ransomware protection
- Device based comprehensive filter and reporting system
Benefits: Block known bad sites, enforce acceptable internet use.
User Education
Benefits: Increase employee resistance to phishing email attacks. After one year of phishing training the failure rate of your employees will drop from 27% to 2% on average.

Once these fundamental risk protections are in place you are ready for customized risk management:
MyITRisk Information Call
- 15 minute call on something you know you want to implement
- or 15 minute introduction of a risk plan
- Fill out survey of your companies landscape
What is My IT Risk? Request IT Risk Assessment to Generate your Risk Scorecard
- Review your landscape
- Recommend needed Risk projects
- Identify your industry security profile
- Review Compromised employee accounts
- Inventory of all your devices and computers
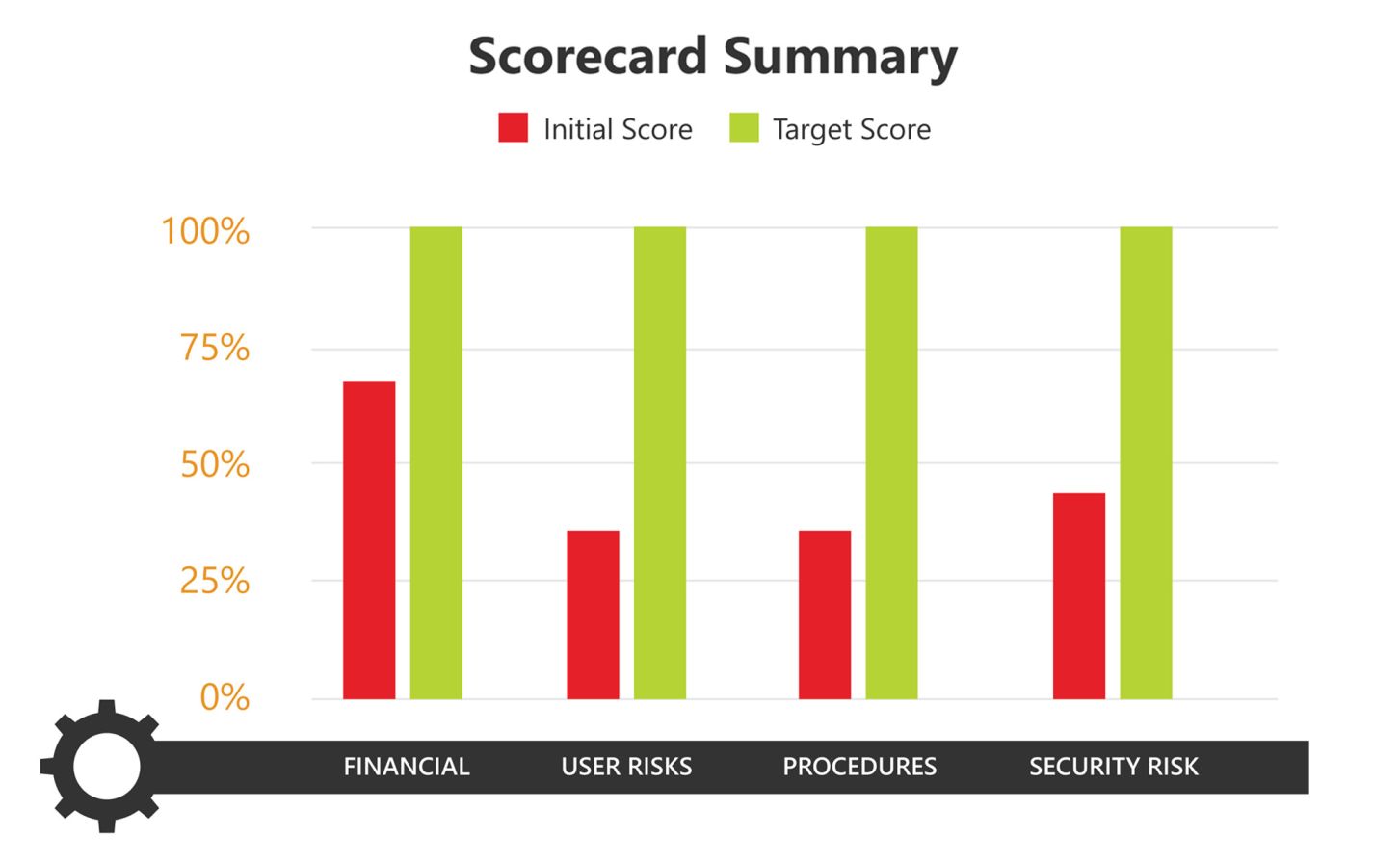
Implement IT Risk Projects
IT Risk Project Cycle: with Project estimates and prioritized implementation
- Review your landscape
- Recommend needed risk projects
- Identify your industry security profile
- Review compromised employee accounts
- Inventory of all your devices and computers
Treatments will lower your Risk in these four areas:
|
Security
|
User Risk
|
|
Documentation\ Procedures
|
Financial
|
- Security Partner Recommendations: Intrusion detection solutions, limiting impact of attacks, partners, detection, penetration tests, introduction meeting. We can recommend a conversation with one of our cybersecurity partners who can provide this highest protection.

