Despite businesses investing in next-gen technologies, phishing threats continue to become more sophisticated and effective according to a new report.
The study from intelligent phishing defense company Cofense shows how threat actors, armed with an ever-growing arsenal of tactics and techniques, continue to tweak their campaigns and enhance their capacity to deliver malware, ultimately getting more messages past perimeter controls to user inboxes.
Among the findings are that between October 2018 and March 2019, 31,429 total threats were reported by end users after delivery to the inbox, these included 23,195 via credential phishing and 2,681 via business email compromise (BEC).

 ms typically notify the recipient that he/she is being sued, and instruct them to review the attached file and respond within a few days — or else. Here’s a look at a recent spam campaign that peppered more than 100,000 business email addresses with fake legal threats harboring malware.
ms typically notify the recipient that he/she is being sued, and instruct them to review the attached file and respond within a few days — or else. Here’s a look at a recent spam campaign that peppered more than 100,000 business email addresses with fake legal threats harboring malware.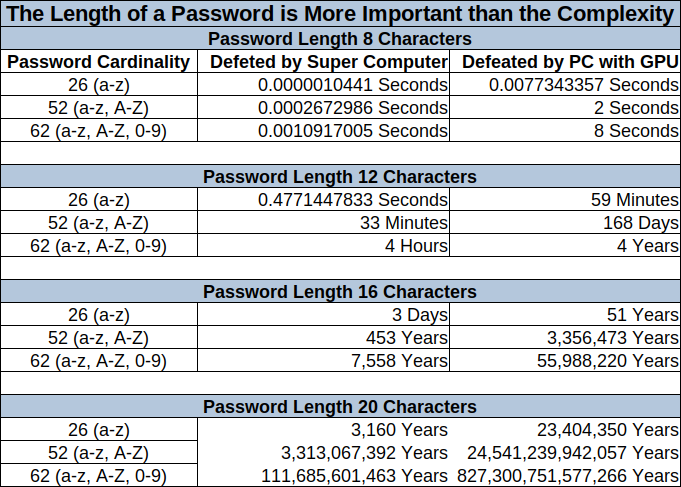
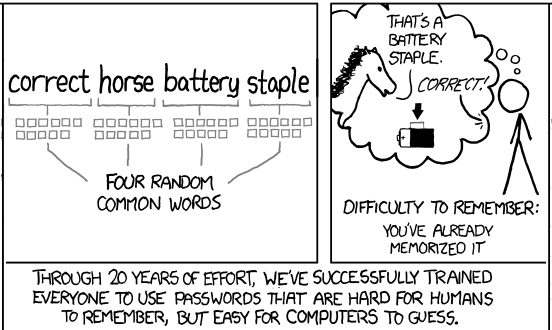 Passwords are (one of) the biggest pain(s) in today’s IT security. They are a factor of life, and the modern lifestyle requires us to have a great many of them. So we need to make sure we’re aware of what is a strong and a secure password. How many times did we enter our information into an online service, registering with our credentials, only to be greeted with a variation of a “Please use a strong password” message?
Passwords are (one of) the biggest pain(s) in today’s IT security. They are a factor of life, and the modern lifestyle requires us to have a great many of them. So we need to make sure we’re aware of what is a strong and a secure password. How many times did we enter our information into an online service, registering with our credentials, only to be greeted with a variation of a “Please use a strong password” message? NIST? NIST is a non-regulatory federal agency whose purpose is to promote U.S. innovation and industrial competitiveness by advancing measurement science, standards, and technology, in ways that enhance economic security and improve our quality of life.
NIST? NIST is a non-regulatory federal agency whose purpose is to promote U.S. innovation and industrial competitiveness by advancing measurement science, standards, and technology, in ways that enhance economic security and improve our quality of life. The European Union (EU)’s General Data Protection Regulation (GDPR) is in full effect, but many organizations still don’t have the processes in place to be compliant. According to an
The European Union (EU)’s General Data Protection Regulation (GDPR) is in full effect, but many organizations still don’t have the processes in place to be compliant. According to an 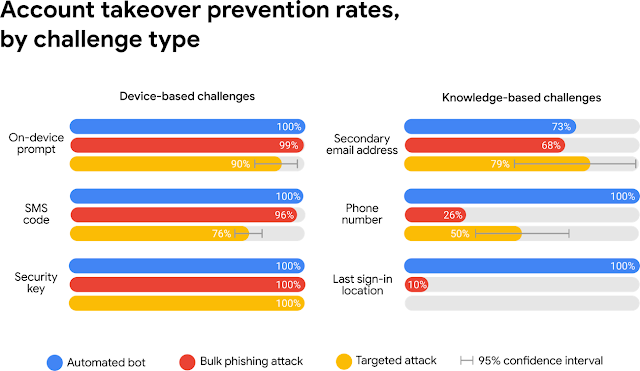
 Does your business have employees? If so, cyber security (and cyber security awareness) are critical to your survival in an industry dominated by growing virtual crime. Certainly, most people know about costly identity theft and reputation-destroying network hacks, which seem to be on the news almost every day. Organizations implement firewalls, comprehensive cyber security defense systems, and sophisticated IT protocols to keep themselves safe from online threats.
Does your business have employees? If so, cyber security (and cyber security awareness) are critical to your survival in an industry dominated by growing virtual crime. Certainly, most people know about costly identity theft and reputation-destroying network hacks, which seem to be on the news almost every day. Organizations implement firewalls, comprehensive cyber security defense systems, and sophisticated IT protocols to keep themselves safe from online threats.