A good password
 Passwords are (one of) the biggest pain(s) in today’s IT security. They are a factor of life, and the modern lifestyle requires us to have a great many of them. So we need to make sure we’re aware of what is a strong and a secure password. How many times did we enter our information into an online service, registering with our credentials, only to be greeted with a variation of a “Please use a strong password” message?
Passwords are (one of) the biggest pain(s) in today’s IT security. They are a factor of life, and the modern lifestyle requires us to have a great many of them. So we need to make sure we’re aware of what is a strong and a secure password. How many times did we enter our information into an online service, registering with our credentials, only to be greeted with a variation of a “Please use a strong password” message?
What would be a strong password? Wikipedia says that “it is a measure of the password’s effectiveness against guessing or brute-force attacks”.
Some websites will even tell you what they consider to be a strong password:
“Please enter at least six characters, at least one capital letter, special character and a number”, while another might just require a “minimum of five characters”. Does this mean one website cares about password strength and security in general more than the other? Absolutely not: in today’s world, every one of us is responsible for improving the general web security. Choosing a strong password is each and every one’s own responsibility.
Say we choose a really strong (and complex) password by bashing our head on the keyboard and producing ‘ao8tu(#URPqw93p48eofklvzJ()AJD)FA’ – this does indeed look like a safe password, but there is the improbability of us remembering it. Now, you might be thinking, password managers!, and you’d be right, but we’ll get to that in a second.
First, let’s see what can we do about our current passwords and passphrases. Are they safe?
haveibeenpwned.com
HIBP is an open and free resource “for anyone to quickly assess if they may have been put at risk due to an online account of theirs having been compromised or “pwned” in a data breach”. Quote by Troy Hunt, the web security expert behind the website. HIBP provide a “Passwords API”, where we can easily check what raw password has already been leaked. HIBP collects most, if not all, data breaches/dictionaries where usernames and/or passwords have been leaked. We can simply enter our password raw and they tell us if and how many times that specific password in question occurs in those leaks. But wait, you must be thinking, why would we want to give our actual passwords to some stranger’s input field on the internet? No matter how supposedly “safe” and “trusting” the service behind that input field is, we should not risk expanding the attackers’ dictionaries. No matter how much we trust them and whoever the author behind the service may be.
Fear not, they do not ask us to give them our actual passwords. We can rely on a concept called k-Anonymity to query a password against the list of leaked passwords, without anyone finding out what exact passwords we queried. To do so, we hash the password we want to query using the SHA1 hashing algorithm, and then send the first five characters of the hash over to the API. The API then checks this hash prefix with all of the pre-computer SHA1 hashes and their prefixes. The response we get from the API is the suffix to the five-character string we submitted, and the number of occurrences of this password in the password leaks. If there are no matches, we get an empty response.
Simple, safe, anonymous.
We can easily try it using the command line (sorry, Windows users!).
Let’s say I want to check if my cat’s name + 123 has already been leaked. First thing I need to do is get it SHA1 hashed:
echo -n Dusty123 | openssl 318bcf7b70297a6ce52c82ad2867c5b0e25318bf
Now, we can query the PwnedPasswords API with the five-character prefix, in my case ‘318bc’:
curl "https://api.pwnedpasswords.com/range/318bc" > hashes.resp
All of the hash suffixes can now be found in the hashes.resp file, and we can simply search through the file for the rest of our hash string:
grep -i f7b70297a6ce52c82ad2867c5b0e25318bf hashes.resp F7B70297A6CE52C82AD2867C5B0E25318BF:675
Seems that there’s a match, 675 of them actually. Ouch.
Now that we know how to check for a potentially unsafe password, let’s see what makes a password safe and secure.
Password entropy
Entropy is a way of measuring the effectiveness of a password in resisting guessing attacks. Entropy determines how difficult it is to guess a password and the measure of this “strength”. That strength is reflected in its length, complexity and unpredictability.
Password entropy can be calculated mathematically and it depends on the password length and the number of possible character combinations.
For a password of length l characters that have been picked at random from an alphabet of xcharacters, the resulting entropy could be represented as l*log2(x),
For instance, if we only used a character set of 26 characters (only lowercase a-z characters), we would get log2(26) ≈ 4.7 bits of entropy per character. For a password that’s 15 characters long, that would be 15 * 4.7 = 71 bits of entropy.
The entropy value is directly tied to the computing power of our generation. As the computing power increases (especially the GPU power) – the entropy of a password needs to increase to maintain its resilience.
Entropy: Factor of length
Let’s say we want to have an eight-character-long password.
If the characters are only:
– digits, there are 10 digits available (0-9), we get 8*log2(10) ≈ 26.57 bits of entropy. ~100 million possible passwords.
– lowercase characters, there are 26 characters in the English alphabet, we get 8*log2(26) ≈ 37.6 bits of entropy. ~209 billion possible passwords.
– upper and lowercase characters gives us a sum of 52 possible characters: 8*log(52) ≈ 45.6 bits of entropy. ~53.5 trillion passwords.
– All alphanumeric and special characters (&;?-_,…) all 94 of them : 8*log(94) ≈ 52 bits of entropy. ~ 6 quadrillion (6*10^24) passwords.
The more characters we have at our disposal, the higher the level of entropy is, as there is a higher number of possible passwords.
According to passwordstrengthcalculator.com, if we took a ten-letter lowercase alphabetic password, it would take a supercomputer™ 0.00071 seconds, or a regular GPU powered PC 5 seconds to defeat it.
Pump that up to 16 characters using the same character set, now a supercomputer™ needs 3 days while a regular PC needs 51 years to defeat the password.
Entropy: Factor of complexity
Humans are not cryptographically secure pseudo-random number generators – meaning that there is a reasoning, structure and a level of predictability on how we build our words and phrases, unlike CSPRNGs (/dev/urandom).
Complexity does increase entropy more when we build our passphrases as gibberish, compared to building them as words, but only to a slight degree. For instance, considering using the same pool of lowercase alphanumeric characters (26), the string ‘hello’ would have lower entropy than ‘hbrtt’, since in the English language, the character ‘e’ often comes right after ‘h’ and is not considered unpredictable.
Expanding our character set increases the overall complexity and entropy of the password, but we might have a much higher chance of forgetting where we put those damned % and & in our SuperSafe%1234&Password. Or was it Super%Safe&1234Password? Gnarh.
Going back to our passwordstrengthcalculator.com, let’s increase the complexity by expanding the character set, adding uppercase characters and numbers.
For a password that is ten alphanumeric characters long, the estimated time to beat is now 4 seconds for a supercomputer™ and 9 hours for a regular PC. Using the same charset password that is 16 characters long, now the times are 7558 and 55988220 years, respectively.
Entropy: Factor of unpredictability
Making our passwords safe from dictionary attacks means being unpredictable when choosing them. If your password is a word of the English language – you are susceptible to a dictionary attack. If the attacker knows you personally, and your password contains something personal, like names of your pets and children, you are susceptible to an attack.
Passwords like ‘P4ssw0rd1234!’ are not considered strong. Even though it is rather long, it has 4 different character sets. Most of the dictionary attackers are taking “l33tsp34k” into consideration when building their dictionaries. Appending 1234 and/or an exclamation mark does add complexity, but it is not something out of the ordinary. Same goes with the “must have an uppercase character requirement”. For most people it’s most likely going to be the leading character.
Since we ascertained that length is a great contributor to entropy, ‘TheLordOfTheRings’ would indeed be high on the entropy score, but it is a common phrase and it is included in every dictionary out there. On the other hand, ‘DogSocksDinnerBlues’ is a phrase which is not that common and does not make much sense, so it would be a good candidate for an unpredictable passphrase. Use common sense on this one.
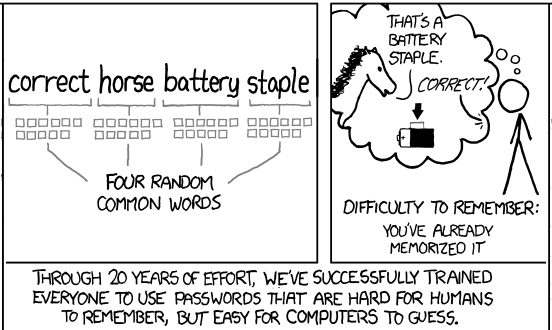
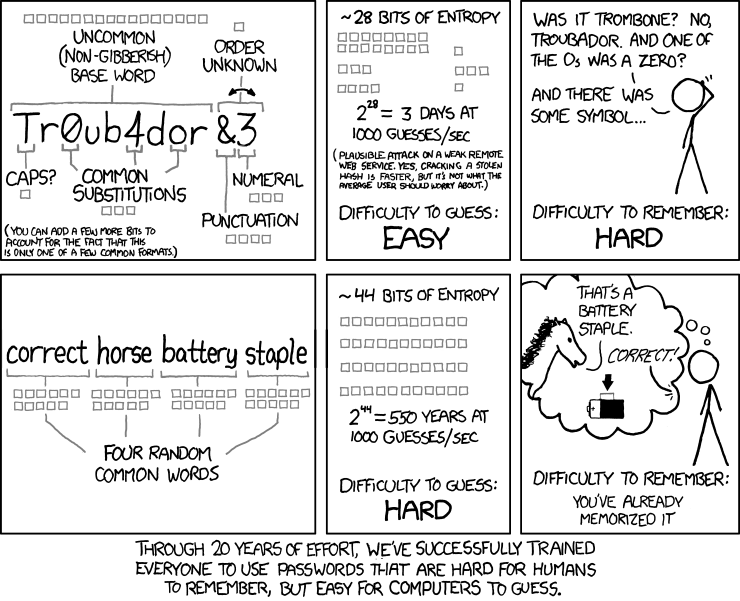
No password strength security blog post is complete without this famous comic and it perfectly demonstrates human nature: we are good at remembering phrases, but really bad at remembering the complexity details.
Choosing a strong password: the Diceware method
So, we learned that for a strong password, we need a good length, complexity and unpredictability. Now, how can we disregard the ‘human’ factor in picking random words? By throwing a dice. Literally.
Diceware is a method for picking passphrases/passwords using regular dice as a hardware RNG. We throw a dice five times, producing numbers in the range from 1-6, and the end result corresponds to a word from a Diceware word list.
A Diceware word list is any list of at least 6^5 = 7776 unique words. The list should contain words which users will preferably find easy to spell and remember.
We need five rolls to get one word, so we would need 25 rolls to get a five-word phrase. The average word length for the most popular Arnold Reinhold’s Diceware word list for the English language is 4.2 characters.
Too short for you? Go for a seven-word phrase. Change the Diceware list. Don’t like the phrase you got? Rearrange it. Roll again.
Whatever you do, this method has already ensured a good passphrase length as well as a great deal of unpredictability.
Choosing a strong password: Password Managers
You don’t want to remember a lot of phrases, but still need to keep a lot of passwords safe and sound? You might want to try out a password manager.
There’s one obvious, single point of failure for password managers: you need a master password (or key) to unlock it. A reasonable and a rational fear is that of
someone getting your master password, but if you’re careful, never use that password on any other service, and you make it secure and long, you should be pretty safe.
All password managers offer storing and encrypting your various passwords and/or usernames and/or websites where you would use them and/or other options.
Most of them are free, but some are unique in what they offer.
For instance, Dashlane is a cross-platform, cloud-synced password manager which enables you to have one app over multiple devices where you would store all your passwords.
If the fact that the passwords are cloud-stored bothers you, no problem. There is KeePass, which is open source and does not store your passwords in the cloud, but locally, in an encrypted file on your machine. 1password is a password manager which integrates with the PwnedPasswords database mentioned above, and notifies you if it detects any of your passwords suddenly appearing in the PwnedPasswords database.
If you’re going to rely on managers, then you should also consider using random password generators. Almost every manager out there offers to generate random passwords for you, with varying complexities and lengths. This way, you don’t have to rely on passphrases since you don’t have to memorize the password, but can employ all sorts of complexities which will expand the character set of your password. Different managers might use different methods of generating random strings with different seeds of randomness, so your best friend, again, is open source.
Conclusion
– Choosing a new password manually should be something we do rarely.
– Ensure that the password you have to choose is safe from both informed statistical attacks and brute force attacks.
– We must ensure that the password we choose is safe and not contained in any existing password leaks.
– Reusing our passwords across different websites or services is dangerous and should be avoided.
– Password managers are our friends and allies, but they are really vulnerable to that single-point-of-failure master password.
